Understanding Secure Coding and Common Security Flaws Through the DVWA Application
1. Introduction
In today’s increasingly digital world, information security has become a key factor for the survival and success of any project. One of the essential methods for ensuring security is through secure coding. Secure coding is not just about writing code that works but also about protecting the system from security vulnerabilities that can be exploited by hackers.
With the ever-increasing number of cyber-attacks and security threats, understanding and implementing secure coding principles is more important than ever. In this article, we will explore the key aspects of secure coding, from basic principles to best practices that help develop secure and sustainable software.
1.1 What is Secure Coding?
Secure coding is a set of principles and practices aimed at minimizing and eliminating security vulnerabilities during software development. The goal of secure coding is to ensure that the software not only functions correctly but also resists potential attacks from external sources.
In simple terms, secure coding is developing software in a way that does not introduce security vulnerabilities.
As the saying goes: “Hearing a hundred times is not as good as seeing once.” We may hear about security vulnerabilities but have never experienced them. Thus, the experience and knowledge would be hard to visualize. Therefore, I will introduce a tool that creates a safe environment for you to experiment with, called DVWA.
1.2 What is DVWA?
DVWA (Damn Vulnerable Web Application) is a web application designed to simulate common security vulnerabilities, helping security experts, developers, and testers practice and enhance their skills in web application security. DVWA provides a safe environment to experiment with attack techniques and defensive measures without harming real systems.
1.3 Installing DVWA
The installation of DVWA is simple and quick through the following Docker article here
git clone https://github.com/digininja/DVWA.git cd DVWA docker-compose up -d
Once installed, the application will run on port 4280
Default Administrator account: admin/admin
Default user account: gordonb/abc123
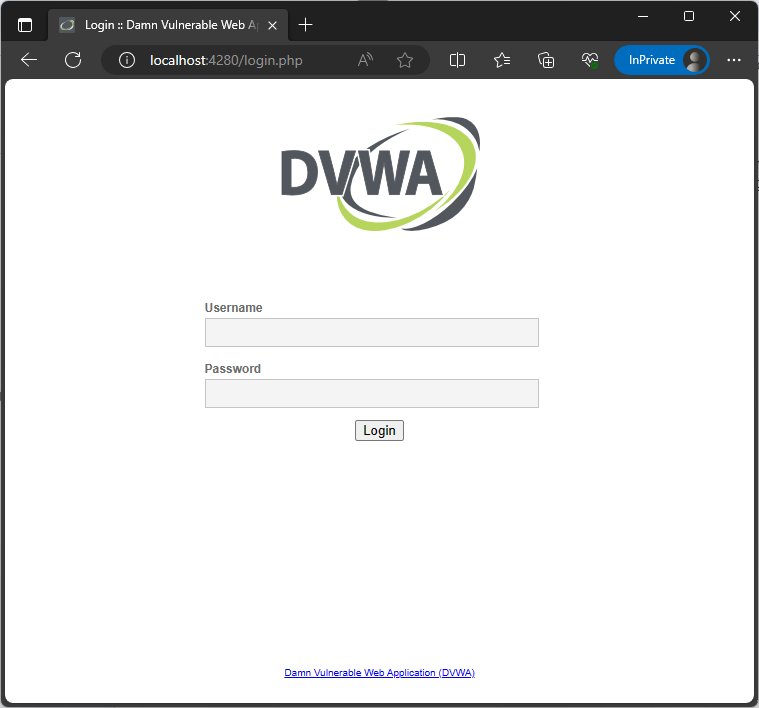
Access and log in to: http://localhost:4280/security.php
Then set the security level to “medium”
2. Common Security Flaws in Web Applications
Next, let’s look at common security flaws encountered when developing web applications.
2.1 Broken Access Control
This flaw occurs when user access control is not properly managed, leading to data being exposed or tampered with.
Refer to the source at Broken Access Control
Example:
Access: http://localhost:4280/vulnerabilities/authbypass/
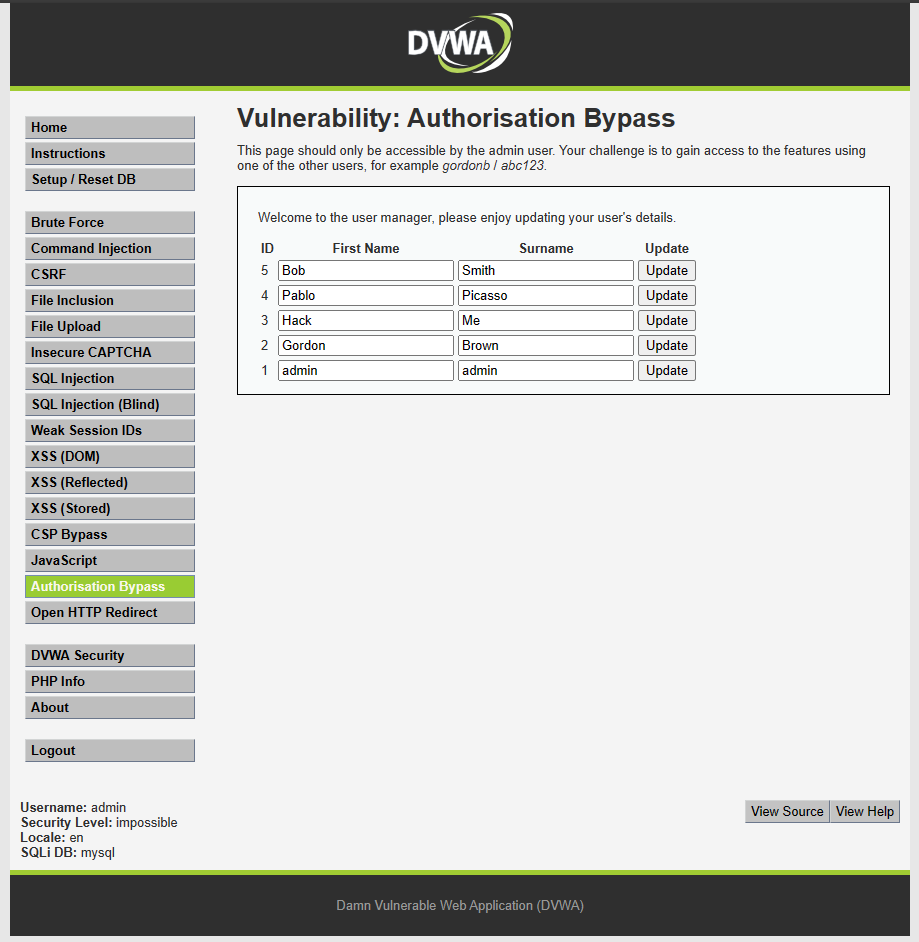
This is the user management page, and only the admin user should have access. After changing the logged-in account to a regular user account, it is no longer possible to access the user management page.
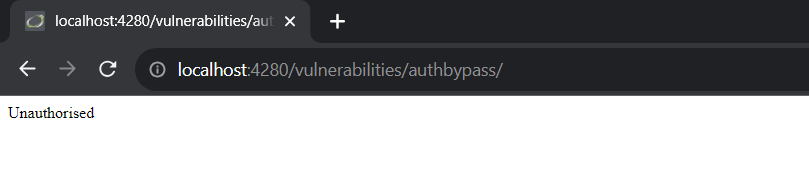
However, the user management page uses an API at http://localhost:4280/vulnerabilities/authbypass/get_user_data.php to fetch data. When accessing this endpoint with a regular account, user information is still visible.
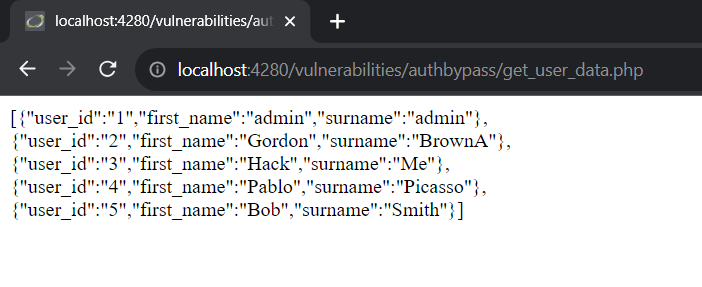
Cause: The developer did not implement proper access checks for the API, resulting in user data being exposed to non-admin users.
2.2 SQL Injection
SQL Injection is a vulnerability that allows an attacker to inject malicious code into the application’s input fields, leading to data loss.
Read more at here.
Example:
Using the account gordonb, access: http://localhost:4280/vulnerabilities/sqli/
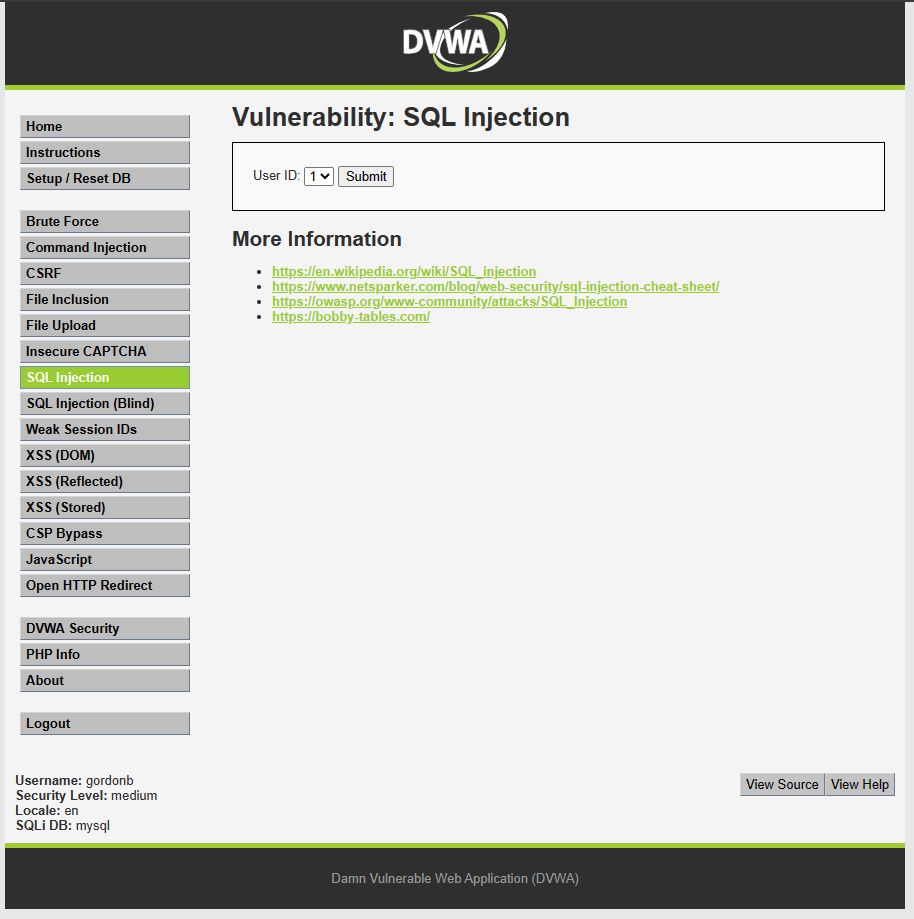
After clicking “Submit,” it will display information for the User with ID 1.
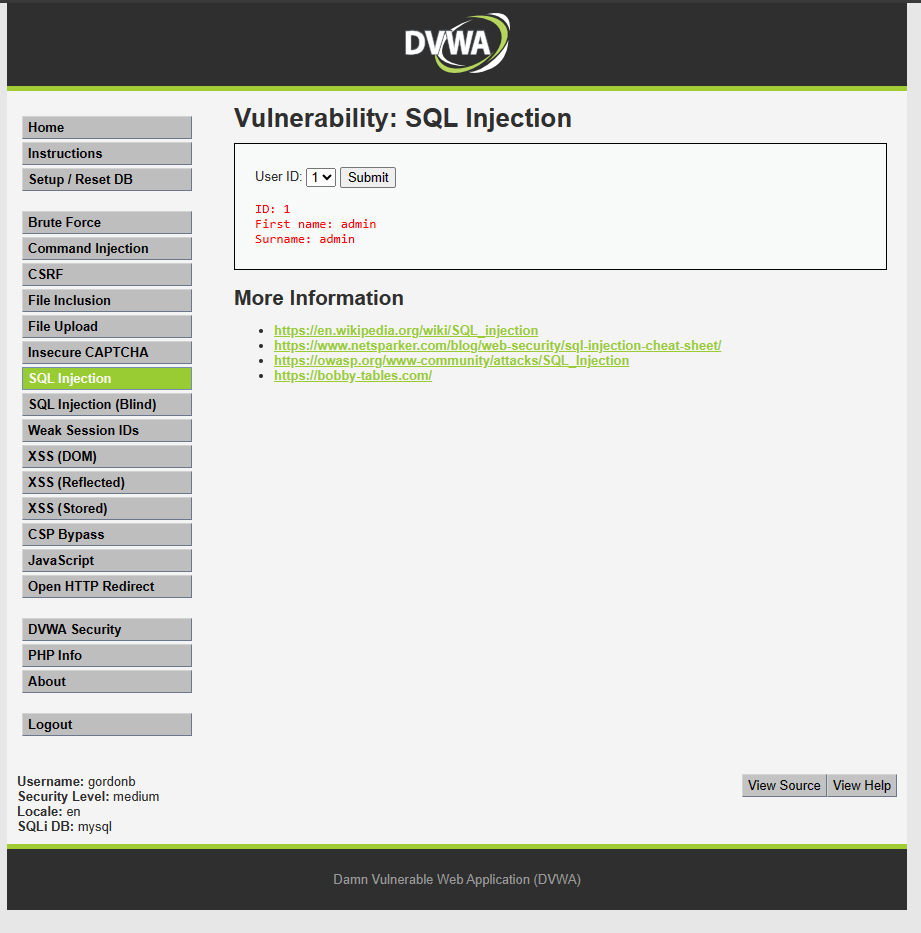
Using “Developer Tool,” change the value of option 1 to:
1 union select version(), GROUP_CONCAT(table_name) AS all_table_names FROM information_schema.tables;--
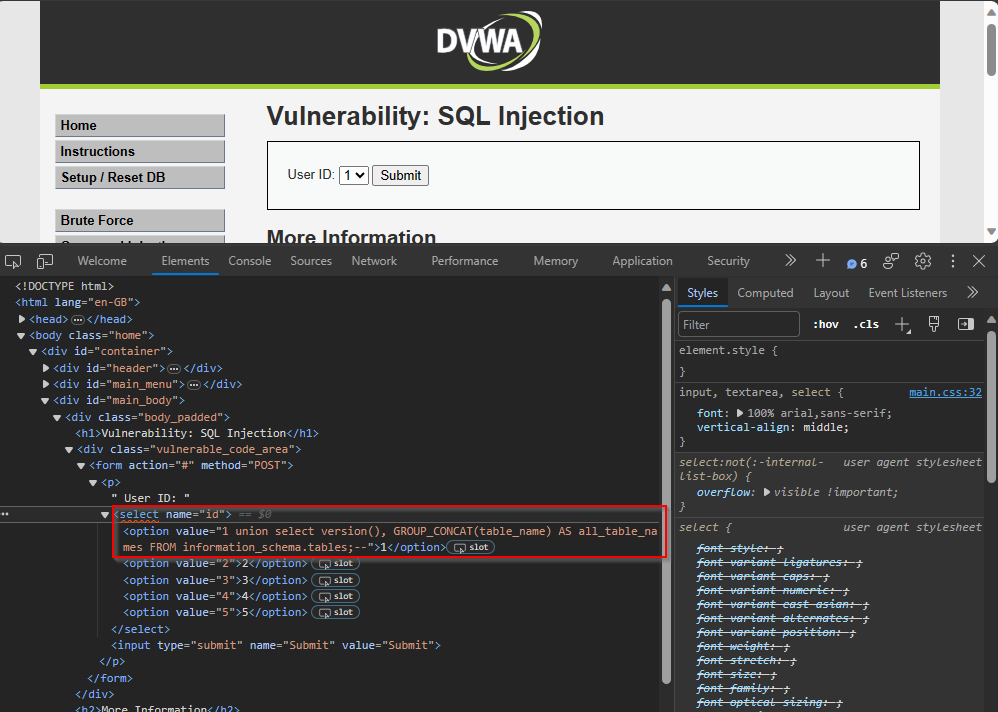
After clicking Submit, it will display all the tables in the database.
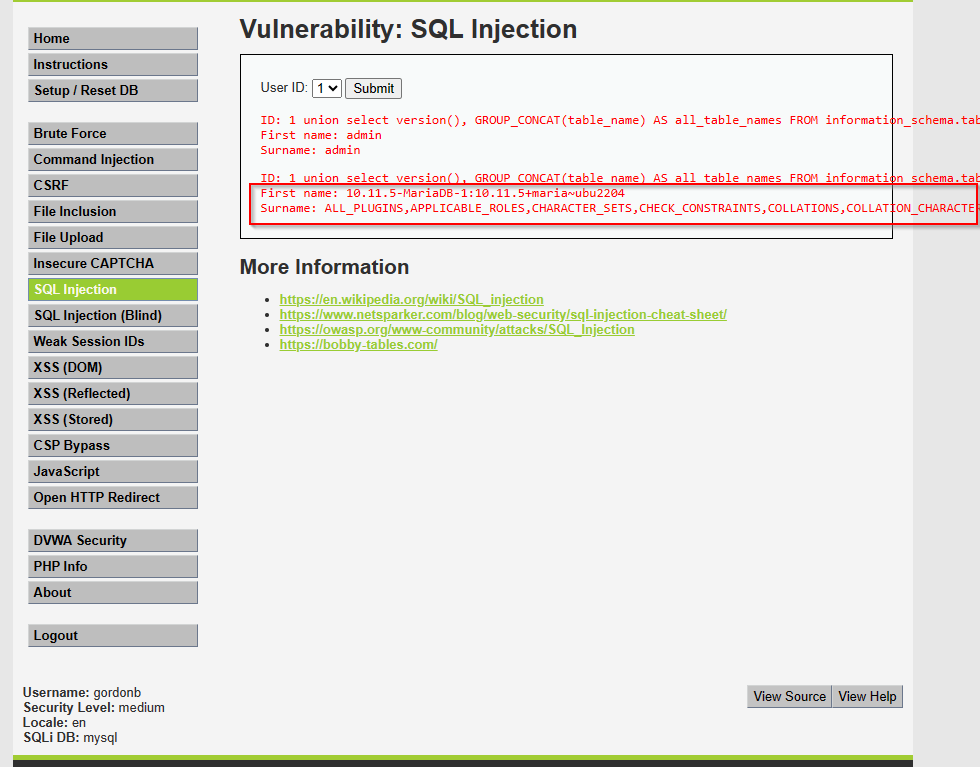
Cause: The developer failed to properly validate input data or the validation was insufficient.
2.3 XSS (Cross-site Scripting)
XSS is a vulnerability that allows an attacker to inject malicious JavaScript code into a website, leading to the loss of user information. XSS is also often used to bypass the browser’s Same-origin policy.
Learn more about XSS (Cross-site scripting).
XSS vulnerabilities are divided into three types: Reflected XSS, Stored XSS, and DOM-Based XSS.
In this article, we will focus on the DOM-Based XSS.
Example:
Access: http://localhost:4280/vulnerabilities/xss_d/
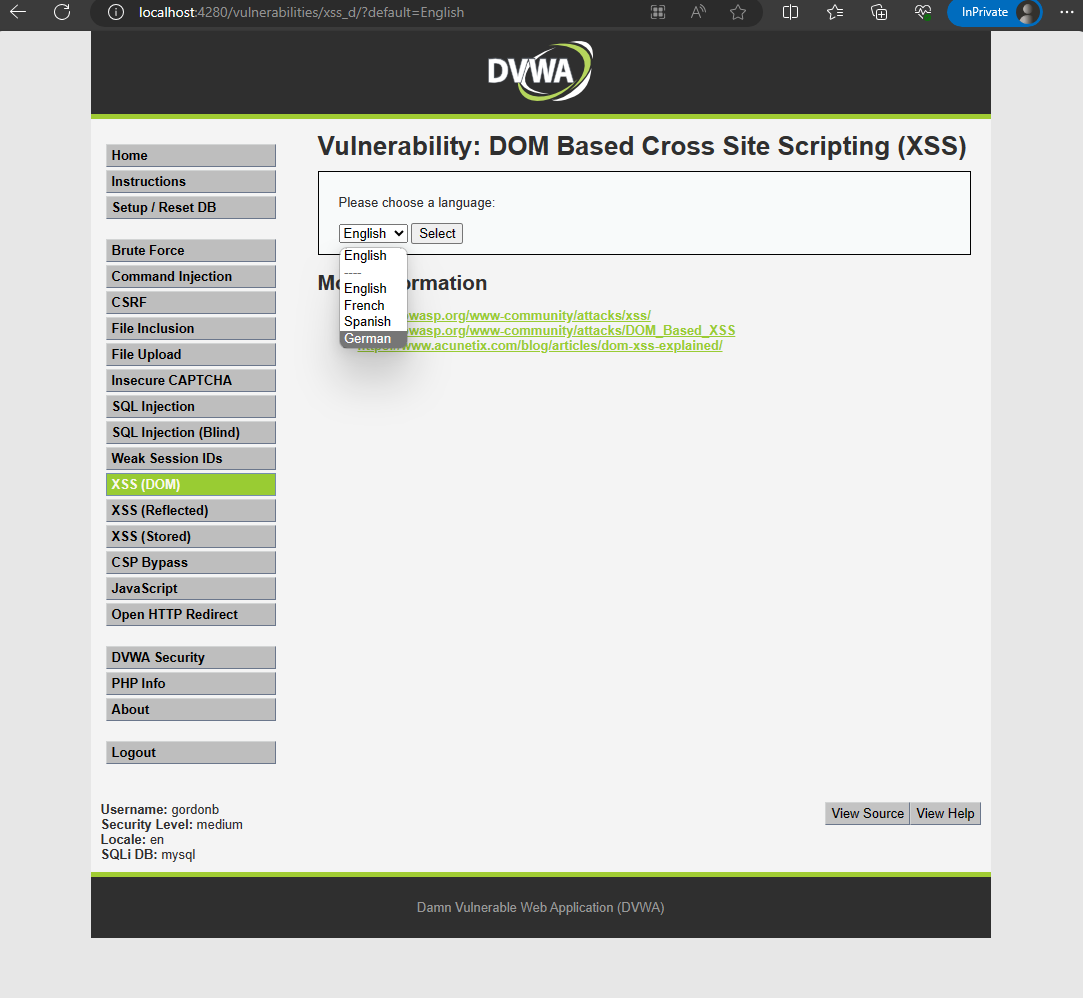
After clicking Select, the URL will look like:
http://localhost:4280/vulnerabilities/xss_d/?default=English
Try changing the default value to any string, and the application will still display the content on the screen.
http://localhost:4280/vulnerabilities/xss_d/?default=ABC
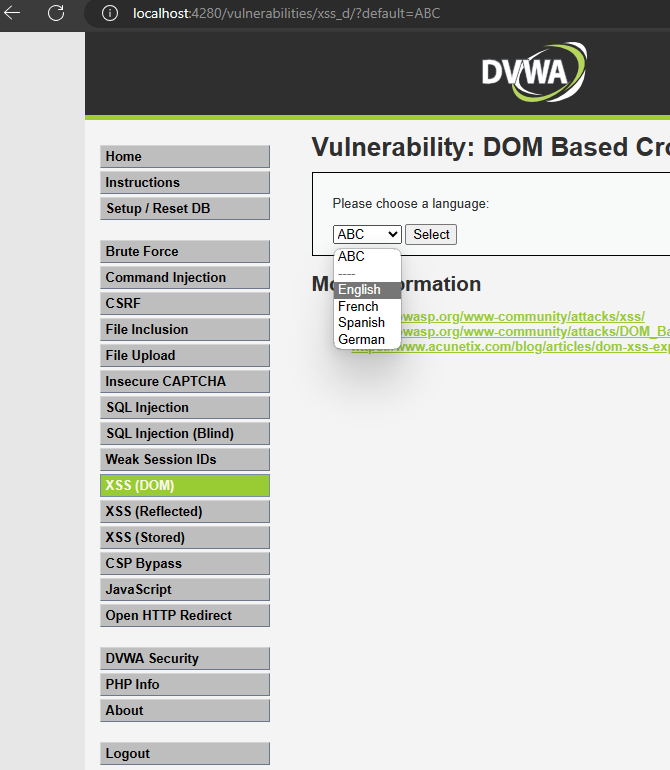
Change the default value to:
ABC></option></select><script>alert(document.cookie)</script><select>
Now the URL will look like:
http://localhost:4280/vulnerabilities/xss_d/?default=ABC></option></select><script>alert(document.cookie)</script><select>
Check the XSS error and you will see that the application blocked invalid input.
However, displaying input data directly on the screen means that an attacker could use other methods to execute JavaScript code.
Example:
Change the default value to:
ABC></option></select><img src="xxx" onerror="alert(document.cookie)"><select>
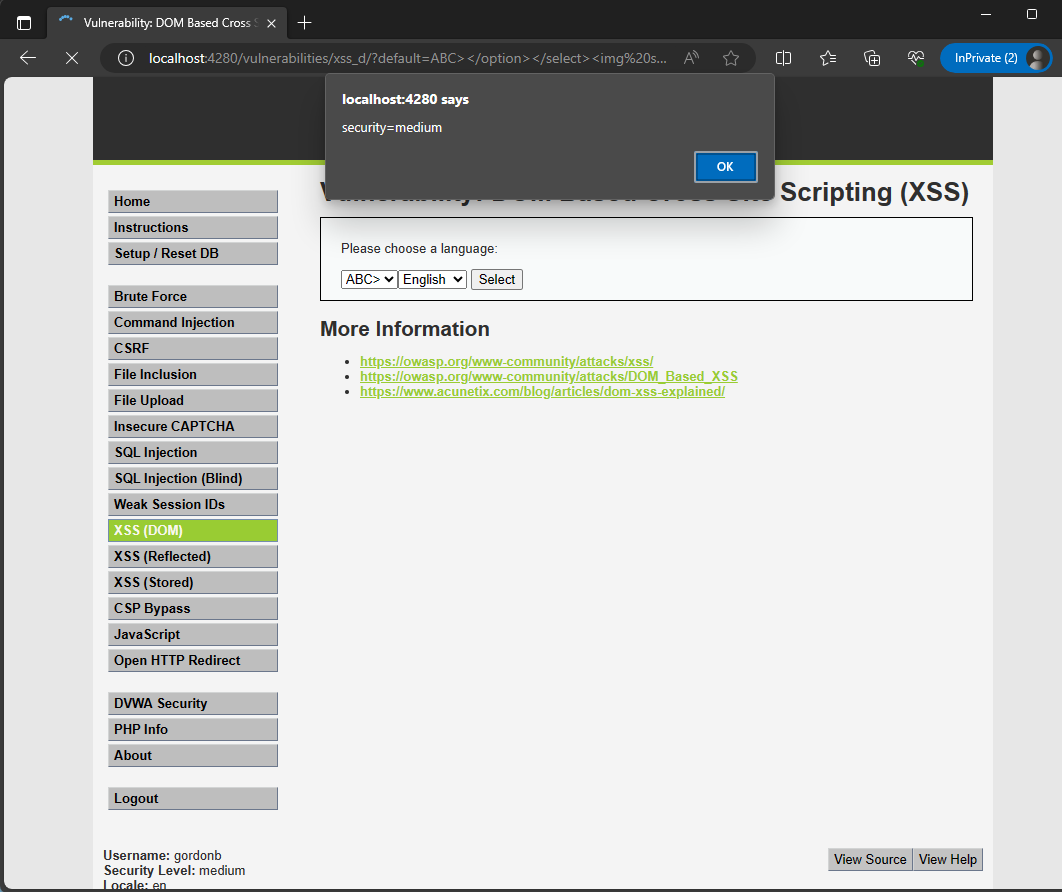
Cause: The developer did not fully validate the input data or handle escaping when displaying user-entered data.
3. Conclusion
It is clear that the flaws mentioned above stem from the failure to properly control input data, so as a developer, always remember: “NEVER TRUST USER INPUT”.
 | Nguyễn Hữu Phận Developer |